
TEE 101: How Intel SGX works and why we use it at Integritee
Integritee uses a technology known as trusted execution environments (TEEs) to process sensitive data off-chain. But what exactly are TEEs and how do they work? In this post, we will take a look at one of the most common & powerful TEE architectures, which we also use at Integritee: Intel Software Guard Extensions (SGX).
Data in different states pose different cybersecurity challenges. End-to-end encryption can provide protection for data while it is in transit, or while it is being stored. But what about data that is currently in use? This is where TEEs come in.
Before an application can execute code on an encrypted dataset, the information must first be decrypted and loaded into system memory (or RAM) to be processed. This provides a window of opportunity for hackers or other third parties to view, intercept or modify the data while it is being processed in an unencrypted state.
Imagine a scenario for instance where you have uploaded some medical records to a database where all data is stored in encrypted form. Now let’s say that your doctor wants to run an application that checks whether a particular drug clashes with any of the existing medications you are currently taking. In order to do this, the application may need admin-level privileges to access the database, decrypt the data and load it into system memory for processing. If this system has been infected with malicious software, however, it may be possible for this rogue application to access the data in an unencrypted state while it is being processed. Intel SGX has been designed to guard against these types of software-based attacks.
SGX is a form of hardware-based encryption that is built-in to many Intel processors released in the last 7 years. It enables system memory to be split into so-called enclaves — private, hardware-encrypted areas within RAM. Enclaves operate a bit like a secret vault where applications can process sensitive data without the risk of it being exposed.
Each enclave is an isolated region within system memory that contains both code and data. Applications that harness this technology can make a call to the TEE using a trusted function — a piece of code created by a software developer that can be executed within an enclave. In the previously mentioned example, for instance, the trusted function might check your medical records within an enclave to detect any potential conflicting medications. The enclave then returns a value to the main application, such as “clash detached” or “no clash detected”.
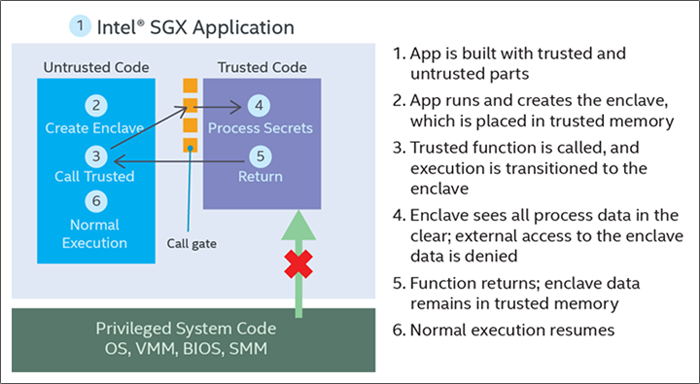
Only trusted functions are allowed to run in the enclave and the memory is otherwise unaddressable, meaning that any other attempt to access enclave data will automatically be rejected by the processor. The important thing to note here is that as encryption is taking place at a hardware level, it protects against software-based attacks. In effect, this means that even if a hacker has access to the entire operating system and BIOS of the system on which the TEE is running, confidential data will remain secret.
In addition, remote users can make use of a feature called “remote attestation”. This enables them to interface with a TEE from a remote system while having confidence that the application has not been tampered with and is running on a genuine TEE. However, this feature requires the service to be registered with the Intel Attestation Service.
So what does Integritee bring to the TEE party you might ask? Integritee democratizes access to the technology by enabling firms to leverage remotely attested TEEs without needing to individually register with the Intel Attestation Service. Blockchain developers and firms can create dApps with Integritee that process potentially sensitive data off-chain in a highly secure way. This can be harnessed for a wide range of use cases ranging from secure oracle services, to faster, more secure digital asset exchanges and much more besides.
To stay up to date with all technical updates to Integritee, follow us on LinkedIn or Twitter.
You Might Also Like
Using AI to Fast-Track Digital Transformation in Governments: Good or Bad?
Cybersecurity: Combining AI & Proxy Tech to Fight Crime
The Digital Euro is the EU’s Next Big Thing — But at What Cost?
Cybercrime: Healthcare & Crypto Hit Hard, Scams on the Rise
K-Anonymity: An Important Tool to Achieve Collective Privacy
An Infinity of Use Cases for NFTs: From Real Estate to Supply Chain
Blockchain and Cybersecurity: Can Decentralization Solve the Biggest Security Challenges?
Public vs Private Blockchain RPC Nodes: What’s Best?
AI & Confidential Computing: Building Trustworthy AI Applications with TEEs
Common European Data Spaces: Fostering Data Innovation & Collaboration in the EU
How Biometric Data Collection Can Be Dangerous — Even When Built With Blockchain
Hyperautomation: The Power of Blending AI, Blockchain, and RPA
Cybercrime on the Rise: Why Is Securing OT Systems Paramount?
For the Greater Good: Using Blockchain for Social Change
Bug Bounty Programs: How Outsourcing Can Help Your Project
DePINs: Harnessing the Power of Connectivity to Build Real-World Applications
MiCA & Other Crypto-Related Regulations: Striking the Right Balance
DEXs on Polkadot: Leveraging the Power of Substrate & Shared Security
Slot Auctions vs Coretime: What’s Changing for Polkadot Projects
DEXs: The What, The Why & The How of Decentralized Exchanges
The Potential of Tokenizing Assets: From Houses to Private Equity & Whisky
Embracing Unpredictability: The Role of Randomness in Blockchain
Uncovering Blockchain Consensus Mechanisms: Proof-of-Stake, Proof-of-Work & Beyond
Decoding CBDCs: Advantages & Challenges in the Digital Monetary Landscape
Unleashing Scalability and Speed: The Importance of Layer 2 Blockchain Solutions
Bear With Us: Blockchain Technology is Still Relevant, Even when Crypto Declines
The Imperative for Privacy in Blockchain: TEEs & Privacy-Preserving Software
How Blockchain is Benefiting Numerous Industries: From Sustainability to Brand Quality Control
KYC in Web3: How DiD is Saving the Day for Projects & Companies
Blockchain in Aerospace: Reducing Costs & Enhancing Efficiency
DAOs: How Fair can Decision-Making be and Why is Private Voting Essential?
Web3 Bounties: Rewarding Developers with Tokens
Digital Twins: Increasing Efficiency Without Compromising Privacy
